SIP DoS/DDoS Simulation
Nowadays as the Internet technologies have overwhelming success over traditional ones, they are still vulnerable since they constantly undergo numerous severe attacks. Undoubtedly one of the most popular fields in the sphere of internet technology is IP-telephony as it covers a wide demand among individuals and businesses.
SIP is generally accepted protocol for Voice over IP (VoIP) calls. A great number of VoIP service providers are available for public internet which means that they can become targets of denial of service (DoS) attacks and excessive calling (TDoS). In case you are an individual IP telephony user, this problem might not interest you to a great extent. However if your business operates mostly via call centers and cloud IP PBX software, or if you provide VoIP services, this can be crucial problem. DoS attacks can block incoming and outgoing calls i.e. which will result in breaking SLA agreements, loss of sales, contacts and eventually reputation. The DoS attack can be initiated by multiple sources (servers, IP addresses), in such case it is called distributed denial of service (DDoS) attack.
We published a public warning about DDoS and IP spoofing, please take a look.
- Percentage of answered calls
- Average delay before answering
- RTP jitter statistics
- Rent a IP spoofing-friendly (unfiltered) server, install SIP Tester with licensed VoIP security features
- Run a simple script with sendspoofedudppacket: send INVITE, REGISTER or OPTIONS packets and spoofing source IP address, Via and Contact SIP headers. You should be able to send up to 50.000 packets per second
- If you know that target server has IP whitelist, you can limit range of IP addresses for the spoofing, down to subnet(s)
- Since source IP addresses are spoofed, the SIP packets should pass SBC's dynamic filters
- Another test to run: modify default CallXML script and insert addsipmalformer elements, to see if your SBC crashes with fuzzed SIP packets. The "addsipmalformer" enables stateful SIP fuzzing; also it enables SIP flooding (e.g. excessive retransmission of SIP ACK packets)
- One more test to run: RTP flooding and fuzzing with setrtpmalformer CallXML element. It randomly modifies bits in transmitted RTP packets (within normal SIP call) and optionally retransmits RTP packets many times, so it should be able to crash your media server
- Contact us if you want us to run the DoS/DDoS tests from our side. We have a way to flood your network with UDP packets from 10.000 IP addresses
Discussion
- IP spoofing is possible only in LAN, unless ISP routers are compromised - true, but the fact is that we can not control all employees of all ISP's.
And hackers can rent a server with IP spoofing, monthly price is less than 160USD (2019). We have managed to contact someone who sells spoofed servers via skype:
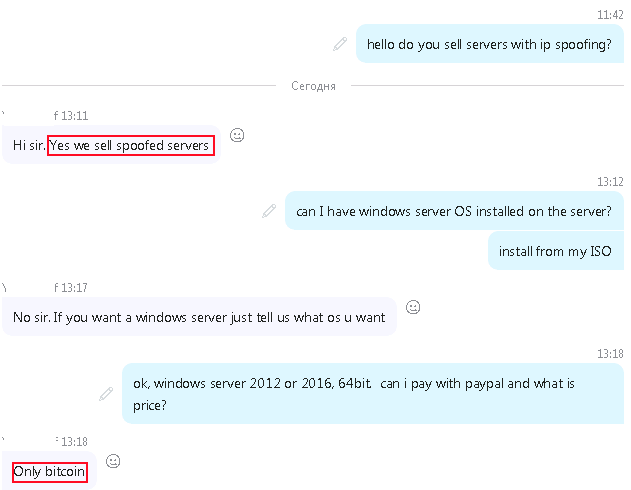
see more details