SIP protocol vulnerability exploit: IP spoofing
Security warning for all VoIP carriers!
If you receive voice traffic from clients via public internet using SIP over UDP protocol (it is default option) - you can be hacked!
Following attacks are possible when a hacker knows your IP address:
- Denial of Service - overloading your VoIP infrastructure with excessive load and causing downtime: all your clients will not be able to pass traffic via your IP address. Using IP-spoofing-friendly internet connection (it is possible today) hackers can set fake source IP address to transmitted SIP packets, in this way bypassing IP blacklists, firewalls, anti-DoS systems (e.g. fail2ban). Source IP address can be set to a random IP, or to your client's IP, if an attacker knows IP address(es) of your client(s). The ip-spoofed attack would look like too many rejected calls from various IP addresses, or from your current clients. The attack can also be performed using OPTIONS, REGISTER, or other packets, in this case it will not get into CDR on your softswitch. Advanced hackers can send malformed/fuzzed SIP packets to your IP, trying to crash your SIP server.
- Toll fraud (if you use IP authentication to receive VoIP traffic from clients) - when a hacker knows both your IP and your client's IP, he can send SIP INVITE
with spoofed IP address same as your client's IP. And the hacker will be able to make unauthorized SIP call as if it is made from your client. Technical details:
in SIP protocol, according to RFC3261 server must send response to address set by "Via" header.
8.1.1.7 Via"Via", "Route", "Contact", "Record-Route" SIP headers can be set to hacker's server IP address. We suppose that following steps are possible by a hacker:
The Via header field indicates the transport used for the transaction
and identifies the location where the response is to be sent. A Via
header field value is added only after the transport that will be
used to reach the next hop has been selected (which may involve the
usage of the procedures in [4]).- Get your IP address and your client IP addresses. If client IP addresses are not known, try to randomly guess correct client's IP
- Send spoofed INVITE with source IP address = your client's IP and hacker server IP in "Via", "Contact" headers, also in SDP
- Authentication procedure analyses source IP address and accepts the call
- SIP stack sends further responses and RTP media not to client, but to hacker's server, according to SIP headers and SDP
How to protect yourself against IP-spoofing attacks?
- If you use IP authentication - make sure that you use complex technical prefix which is unknown to hackers
- Pass VoIP traffic over VPN with encryption
- Use secure transport - run SIP over TLS (SIPS) or at least SIP over TCP. Encrypt RTP (voice traffic) too, using SRTP.
Is it possible to send IP-spoofed packets over public internet?
It is easy to send spoofed IP packets across local network (LAN).
But if you try to send a UDP packet with fake source IP address through your current internet connection, most probably it will be blocked, because internet providers have configured their IP switches correctly.
What happens if some employee inside ISP removes the anti-spoofing filter, connects a small device to the switch and sends IP packet with fake IP address?
Top-level internet carriers are not able to filter source IP addresses, and the packet will be transmitted to destination address via internet. There is a good article about it written by Cloudflare.
We have managed to contact someone who sells spoofed servers via skype:
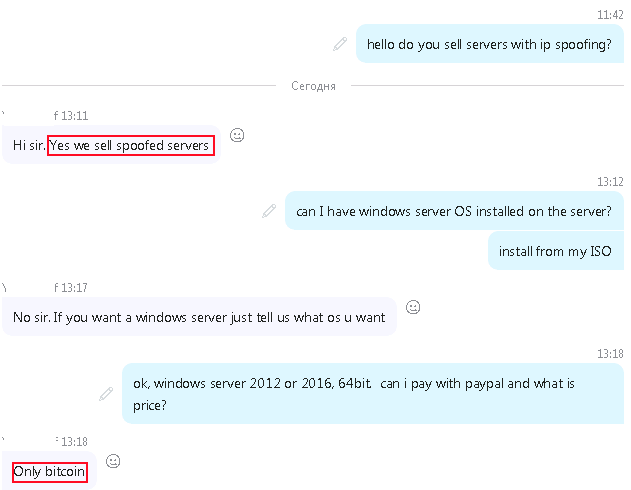
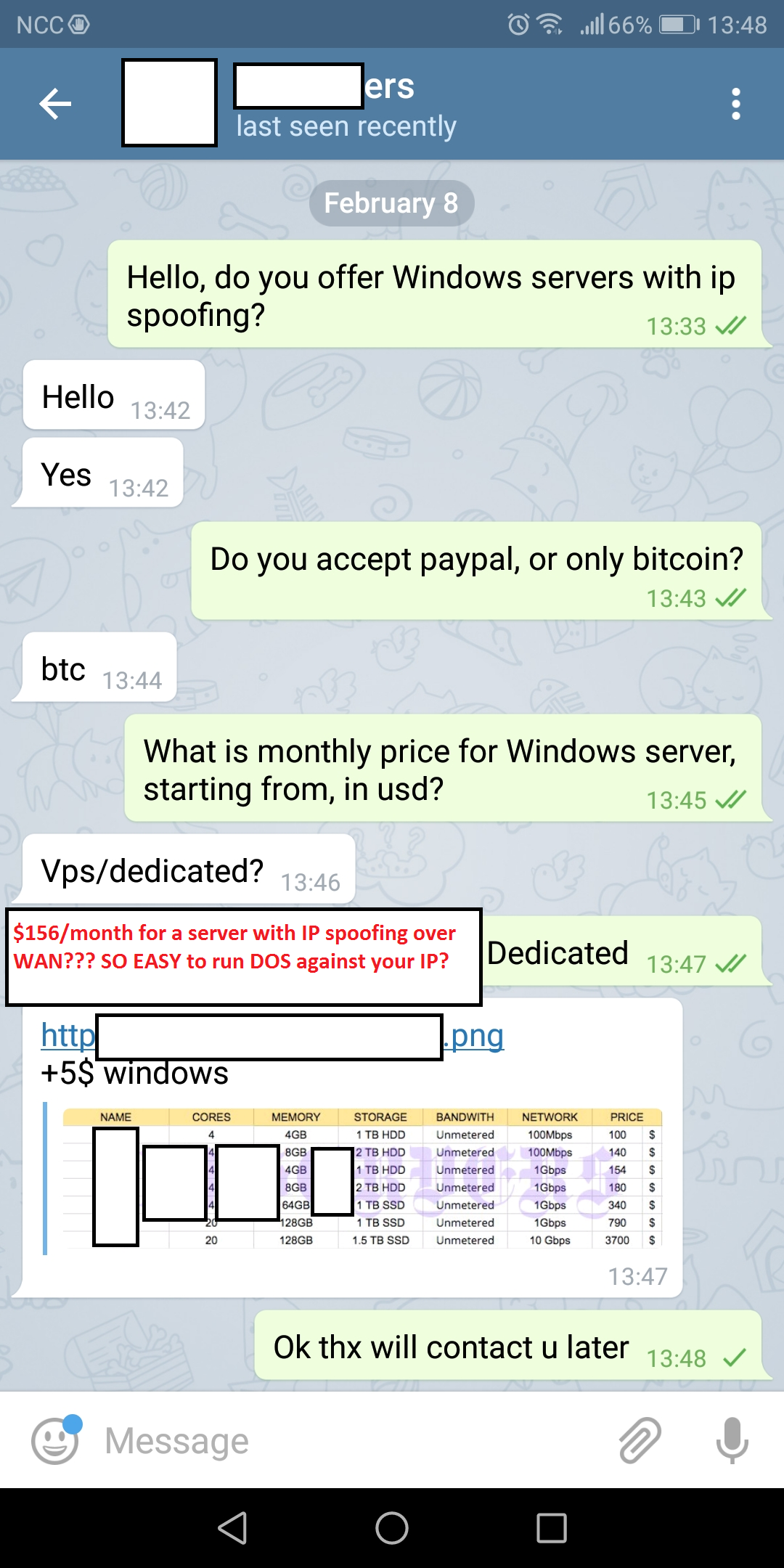
and via telegram (at least 4 places where one can rent spoofing-friendly servers, from 160USD/month:
Get consulting or test your softwitch: sales@startrinity.com or skype asv128
and via telegram (at least 4 places where one can rent spoofing-friendly servers, from 160USD/month:

Who we are: we are startrinity.com VoIP software developers, our products are StarTrinity SIP Tester and VoIP Security Test Suite. See our VoIP security updates