FreeSWITCH penetration testing / hacking
Our objective is to test stability of various SIP/VoIP servers, in order to make sure that the software is stable against VoIP attacks. Here we publish results of tests with FreeSWITCH. For our tests we use our penetration test suite.2018-11-18 - FreeSWITCH 1.8.2 - DOS attack with malformed SIP packets
We have downloaded latest version 1.8.2, compiled it with Visual Studio 2017, applied minimal configuration to the FreeSWITCH:- File conf\sip_profiles\external.xml: modified entry
<param name="sip-port" value="5080"/>(set SIP port to 5080)
- File conf\dialplan\public.xml: added entry
<extension name="public_did"> <condition field="destination_number" expression="12183456789"> <action application="answer"/> <action application="bridge" data="sofia/internal/freeswitch2siptester@192.168.10.6:5070" /> </condition> </extension>Here we route SIP calls from the FreeSWITCH (192.168.10.4:5080) back to our SIP Tester (192.168.10.6)
- Set XML entry log level = ERR in some other xml configuration files:
<param name="loglevel" value="ERR"/>We don't want the excessive logging to affect results of our tests
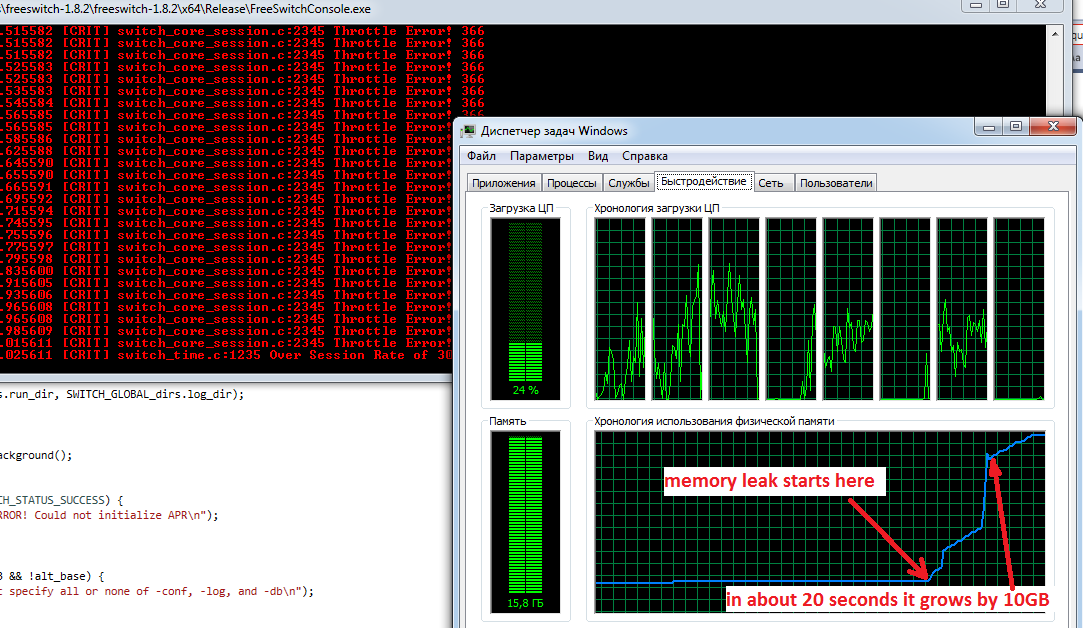
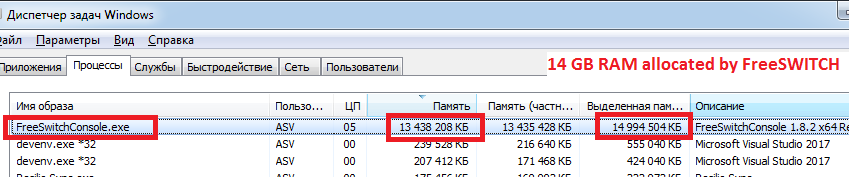
In a real environment I think the watchdog will restart the Freeswitch. If the SIP DOS attack continues, it will continue to restart. It means interruption of 24/7 operation of the softswitch. Not good.